Sản phẩm IP đầu tiên của bên thứ ba được chứng nhận ISO/SAE 21434 dành cho an ninh mạng ô tô
Increased processing and connectivity in automobiles are cranking up the priority for advanced cybersecurity steps to keep roads safe. Electronic vehicle interfaces, including 5G/6G, Bluetooth, Wi-Fi, GPS, USB, CAN, and others, offer convenience features for drivers and passengers, but open numerous attack vectors for hackers. Many vehicles now provide over-the-air (OTA) update capability for infotainment systems and mission-critical vehicle software, adding to security concerns. Synopsys has taken a bold step in achieving third-party ISO/SAE 21434 certification for its ARC HS4xFS Processor IP, with more 21434-certified IP in the pipeline.
Second certification effort for ARC processor IP in automotive
Automotive industry observers are likely familiar with ISO 26262, the functional safety (FuSa) standard that assesses system behavior and any potential degradation in the face of hardware and software faults. ISO 26262 was the initial automotive standard certification focus for the Synopsys ARC Processor IP family, and many ARC core variants, including the ARC HS4xFS Processor IP, now contain FuSa features certified to ASIL D levels.
Cybersecurity presents similar concerns for automotive designers but requires defining a substantially different framework. “For starters, a comprehensive cybersecurity approach for automotive needs much tighter communication between automakers and suppliers,” says Ron DiGiuseppe, Automotive IP Segment Manager for Synopsys. “It also requires commitments at the executive level in creating dedicated cybersecurity assurance teams that partner with the product development teams, overseeing due diligence and working hand-in-hand with product development teams to enforce processes for creating and maintaining ISO 21434-certified IP.”
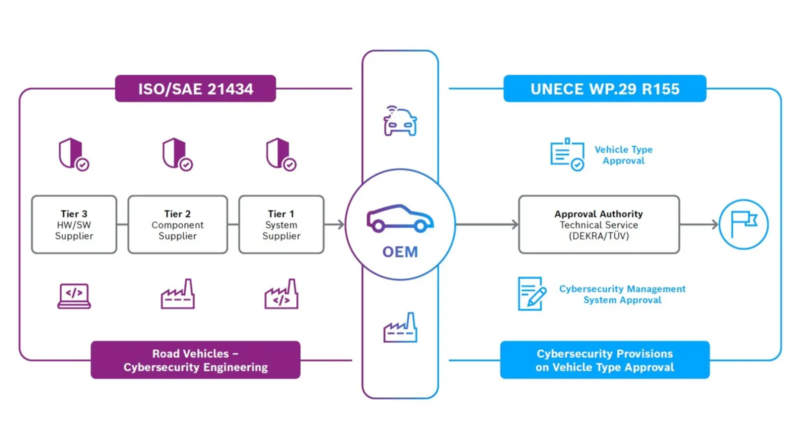
ISO/SAE 21434 “Road vehicles – cybersecurity engineering” defines such a framework, standardizing roles and responsibilities for various groups during different stages of automotive product development. It comprehensively addresses policies, processes, and procedures in a Secure Development Lifecycle (SDL) with specific criteria that each stage of development must meet before proceeding.
Initial support for ISO 21434 from European stakeholders
A broader European effort is piggybacking on ISO 21434, seeking to harmonize vehicle regulations. UNECE WP.29 extends into cybersecurity and software updates with two recent additions, R155 and R156. R155 sets up a path with uniform provisions for approval of vehicles designed to ISO 21434 and its cybersecurity risk management system.
“Manufacturers and car owners have a vital self-interest in protecting vehicles against cyberattacks,” says Meike Goelder, Product Management Cybersecurity at Bosch (see the full Bosch video “100 Seconds: The Importance of Cybersecurity“). “Attacks aim at manipulating safety-critical parameters, violating privacy by stealing customer data, or even hijacking a car, and new ways of attacking whole fleets only multiply the danger.” She sees both ISO 21434 and UNECE WP.29 R155 helping ensure the cyber compliance of cars.
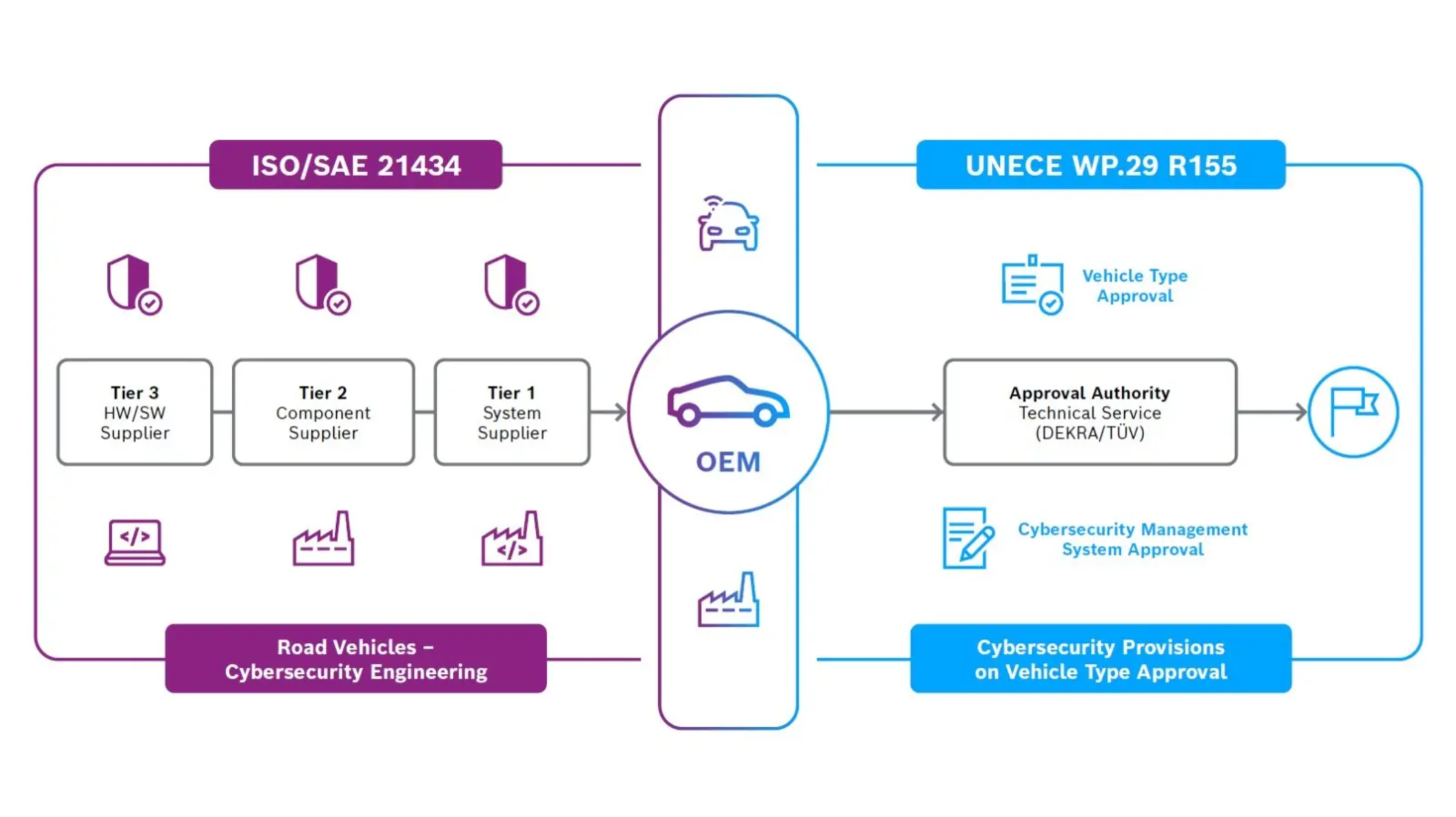
image courtesy Bosch
DiGiuseppe points out that although UNECE WP.29 R155 is a European effort, taking the lead in defining an approval process, it sets a de facto standard for auto manufacturers selling in global markets. “To help ensure automakers and their suppliers comply with cybersecurity risk management, we selected an appropriate product, the ARC HS4xFS Processor IP, aligned our organization and processes, assessed for compliance, and obtained ISO 21434 third-party certification by SGS-TṺV Saar expediently.”
Installing cybersecurity risk management engineering processes
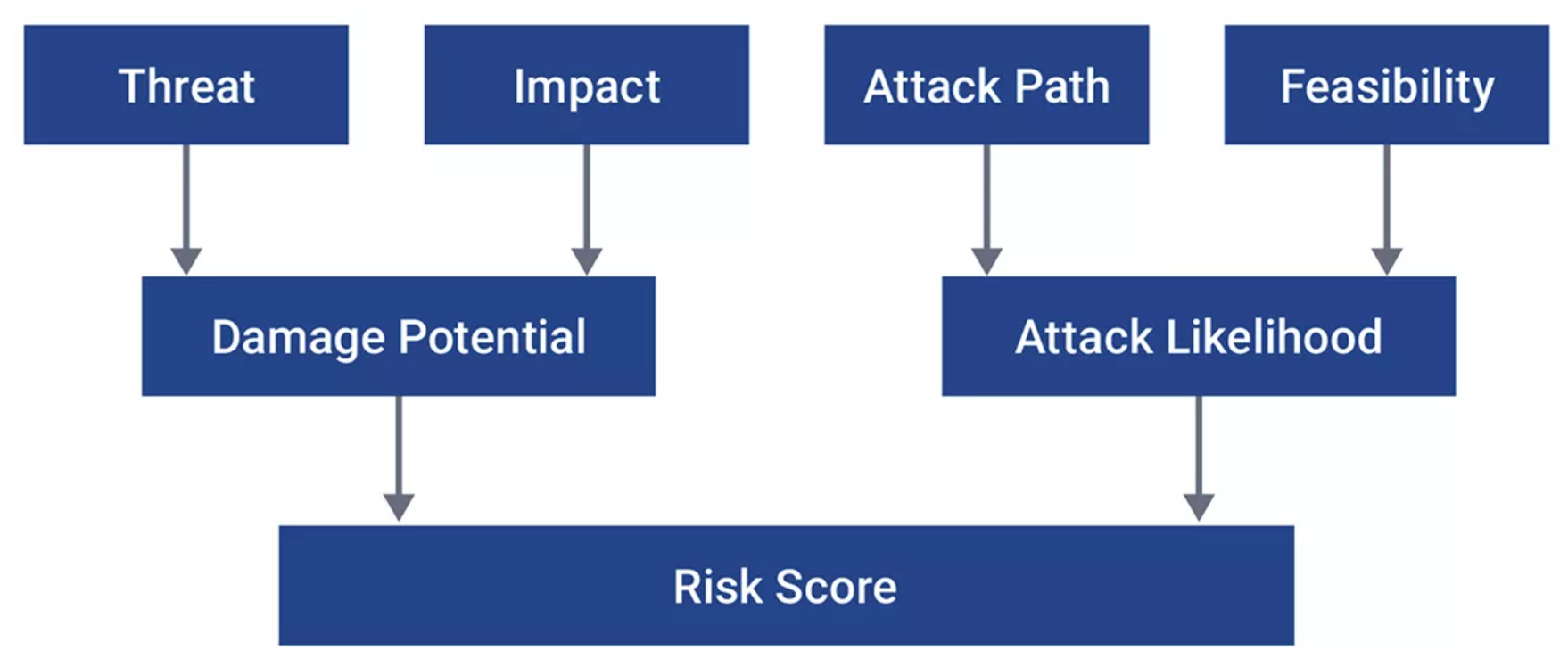
Achieving ISO 21434 certification involves two distinct phases: assessing the potential vulnerability of a product and providing an organizational structure for ongoing incident response should any occur. Vulnerability is approached by a Threat Analysis and Risk Assessment (TARA), creating a risk score based on four factors. Having a risk score helps drive informed decisions about treating risks, either through the development process or with specific modifications to a product.
image courtesy Synopsys
We asked DiGiuseppe the obvious question: did the ARC HS4xFS Processor IP require any modifications to become ISO 21434-certified IP? The assessment found no security vulnerabilities, which SGS-TṺV Saar confirmed in their audit, so no changes were needed. He indicates other products, including ARC NPU and ARC-V processor and interface IP, are in the certification pipeline, and they hope for similar outcomes but are ready to make any necessary product modifications.
The Synopsys cybersecurity risk management engineering processes include the Security Development Lifecycle, Security Risk Assessment, and IP Security Incident Response Team. As is often the case with systems standards certification, vulnerability management expertise is valuable to help identify, diagnose, and communicate vulnerabilities and the best mitigation approach. “This is the first IP product third-party certified to ISO 21434 in the industry – and we now have processes and teams in place to certify more of our IP products,” DiGiuseppe concludes. This breakthrough is welcome news for SoC designers, whether at automakers or third-party suppliers, who must get ISO 21434 certification with their products. More background on the ISO/SAE 21434 standard and the Synopsys ISO/SAE 21434-certified IP details are online.
Technical bulletin on ISO/SAE 21434 by Ron DiGiuseppe:
The Promise of ISO/SAE 21434 for Automotive Cybersecurity
Details on Synopsys’ industry-first third-party ISO/SAE 21434-certified IP product:
Synopsys Advances Automotive Security with Industry’s First IP Product to Achieve Third-Party Certification for ISO/SAE 21434 Cybersecurity Compliance
Share this post via: