Đối mặt với những thách thức trong việc triển khai Mật mã hậu lượng tử
While researchers continue a march for more powerful quantum computers, cybersecurity measures are already progressing on an aggressive timeline to avoid potential threats. The urgency is partly in anticipation of a “store-now-decrypt-later” attack where compromised data, seemingly safe under earlier generations of encryption technology, is gathered and kept until quantum computers grow powerful enough to enable future decryption. Hardware lifecycles are also on the minds of many, where chips developed using classical pre-quantum algorithms will abruptly become obsolete. Secure-IC outlines the approach needed to confront the industrial challenges of implementing Post-Quantum Cryptography (PQC) in its new white paper.
Revisiting the algorithms and planning a transition
RSA became the de facto standard in encryption technology in the late 1970s. It combines short decryption times with unreasonably long crack times thanks to long key lengths. Crack time estimates in hundreds of years were the best guess based on the computing power of the day – mainframes and mini-computers. For every measure, there is a countermeasure, and it only took two decades for Shor’s algorithm to emerge, theoretically rendering both RSA and elliptic curve cryptography vulnerable. In practice, Shor’s algorithm would need to run on a much more powerful computer to crack encryption in a reasonable time. Despite processing power advances along Moore’s law, RSA cryptography has remained safely beyond cracking.
Quantum computing changes the curve with an exponential increase in computational power as the number of qubits scales. Soon, quantum computers could offer enough operations per second to cut crack times dramatically for classical encryption methods. That should not be a surprise – classical encryption algorithms remain fixed while computing power grows yearly, which means new algorithms will be needed if encryption is to stay safe.
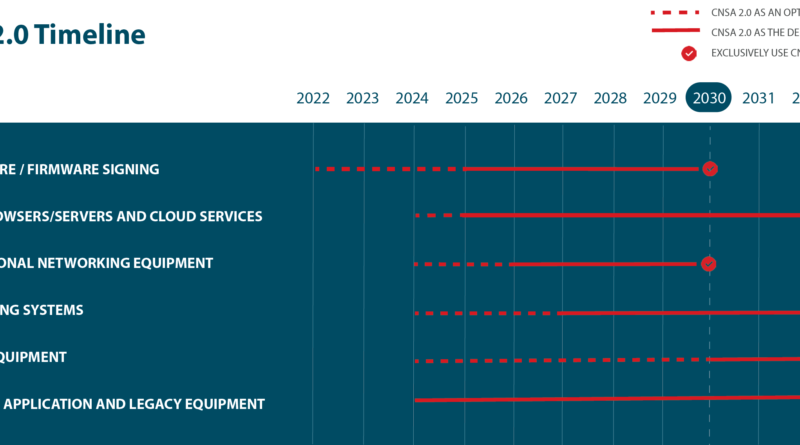
NIST has pursued PQC algorithms since 2016, announcing its first round of selections in July 2022. From those selections, the NSA issued its PQC recommendations in the Commercial National Security Algorithm Suite 2.0 (CNSA Suite 2.0) with timelines for modernizing six classes of systems and a target of having all systems PQC-enabled by 2033.
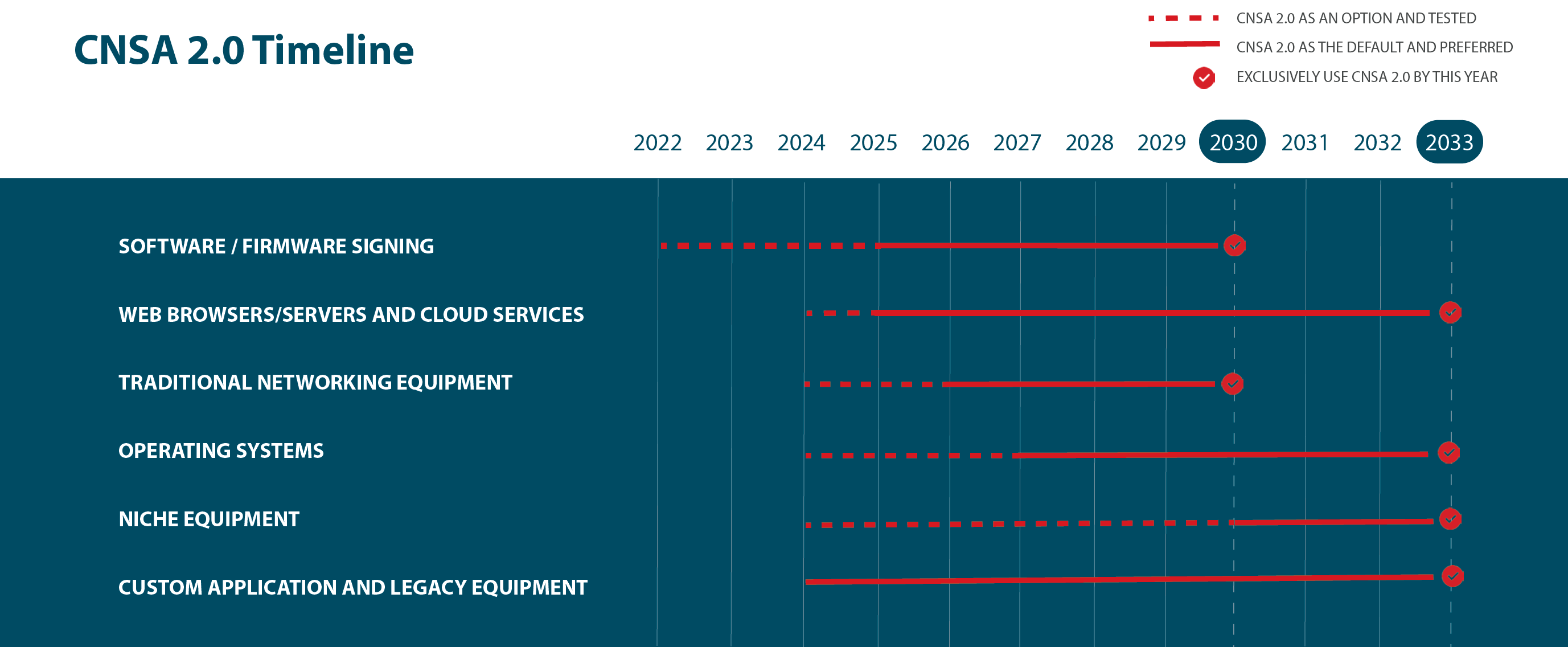
With the NSA’s initial software/firmware signing and cloud services goals looming in 2025, developers need to get moving with PQC technology and IP, forcing the discussion from theory to practice. Agencies in Europe – including France’s National Cybersecurity Agency (ANSSI) and Germany’s Federal Office for Information Security (BSI) – and Asia have issued similar timelines for approaching the PQC transition.
Projecting PQC theory into practical implementations
Secure-IC devotes the balance of its white paper to practical implementation challenges. High on the list is performance, particularly embedded device performance, as many more devices connect to the internet and must encrypt and decrypt traffic for security. Also on the list is hybridization, where classical and PQC algorithms exist in systems simultaneously. Another point is the existence of new cryptographic primitives in PQC and the associated concerns with design, integration, licensing, and interoperability. Their last point is certifications, where industry and regional differences complicate the landscape and usually mean addressing multiple certification efforts to field a product in various applications and markets.
In developing its PQC-ready technologies, Secure-IC created a hardware accelerator and software library that delivers a complete solution to address these challenges. Their hardware architecture manages impacts on power, performance, and area (PPA) for enabling embedded devices with PQC. Their software provides configurable modules for both classical and post-quantum algorithms. Secure-IC’s solutions have achieved several certifications, including those for the automotive industry.
To download a copy of the white paper and see how Secure-IC solutions face the challenges and help developers safeguard digital assets, please visit the Secure-IC website:
Share this post via: